I am assuming by now everyone what happen when we use Symantec anti virus on PVS streamed virtual machine. This has been discussed in detail in the article from Symantec. Something to quote from
- Loss of communication between provisioned Symantec Endpoint Protection clients and manager.
- Duplicate client entries appearing in the Symantec Endpoint Protection Manager (SEPM) every time a provisioned client is rebooted.
- Provisioned Endpoint Protection clients switching between SEPM client groups, receiving wrong policies, not maintaining current definitions, etc.
To fix this Symantec suggest following :
- Disable Tamper Protection on the SEP client; this must be done to allow the file and registry changes in steps below.
- Close any open SEP Client GUIs, go to the command line, navigate to the Symantec Endpoint Protection program files directory and stop the SEP Smc service smc -stop
- Set SEP service to start manually.
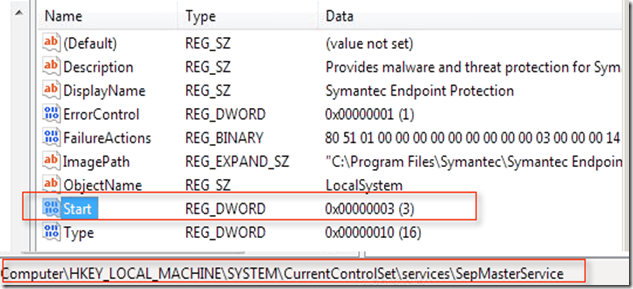
In SEP 12.1, set HKLM\SYSTEM\CurrentControlSet\services\SepMasterService\Start=3
In SEP 11.x, set HKLM\SYSTEM\CurrentControlSet\services\SmcService\Start=3
Now if you do not follow above two steps you wont be able make changes in the registry. If attempted following will be the error

So we must follow steps as mention above and first of all disable Tamper protection. But how will you do so because as soon as you stop Symantec service as mention above you wont get GUI and if client is managed one this will be grayed out by default.

So how to set the SEP service to manual ?
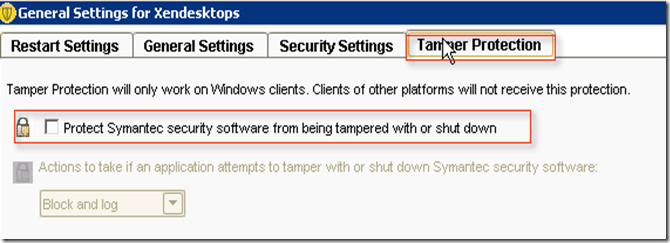
a) From SEP server browse to Client and then choose the container for which we have to disable Tamper protection. Choose "General Settings"

b) Under general setting you can find Tamper Protection option uncheck the box for making changes from client side
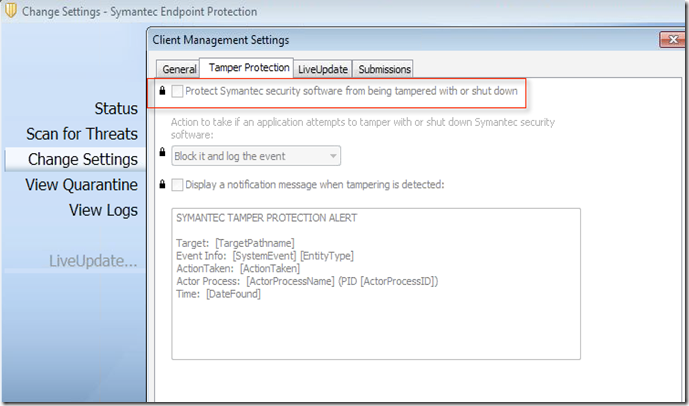
c) Now when you check the client side it will be disabled
e) Now when you try to make registry changes then it will allow you to make the changes also you can verify that SEP service has been set to manual
Revert back the change made in step b) . Also now we have to implement the script for machine startup . Copy the file under netlogin folder on Domain Controller and then apply the policies like this

Not sure why people can not write simple plain KB understood by everyone .















