NOTE: This is not for fun or to stole password of a Administrator but for purpose of recovering “Admin” password incase if you have lost the password for some reason.
So the story goes like this,
My company wanted me to connect laptop to the VPN so that all the patch update happens. Finally I decided to connect it. *Crap * after the VPN was disconnected I locked my PC and thought morning I will check it again. Now I can not login to the PC using Administrator. Our global support tried all the permutation and combination to login and nothing worked out. They asked me to image the machine and I do not wanted to do so because I have to go through all the setup again. I called my college and asked if he has any image CD (He has the similar problem a while ago). He has DELL recovery CD which he handed over to me. So I planned to secure my data by installing another copy of XP and then copy all my data. Now I was confident that even if I loose all the data I am not bothered.
Recovery process 1: (Linux Based)
http://home.eunet.no/pnordahl/ntpasswd/
I used the above program and then created a bootable USB. There is a way to create bootable USB which you can find it on read me file on ISO.
http://www.4shared.com/file/46083366/29dae170/cd0709271.html
1. Get the machine to boot from CD (or floppy)
2. Floppy version need to swap floppy to load drivers.
3. Load drivers (usually automatic, but possible to run manual select)
4. Disk select, tell which disk contains the Windows system. Optionally you will have to load drivers.
5. PATH select, where on the disk is the system?
6. File select, which parts of registry to load, based on what you want to do.
7. Password reset or other registry edit.
8. Write back to disk (you will be asked)
Now I provided all the information and did the point 8 but to my surprise it did not save the password. No matter what I do password was not getting changed. Something wrong with SAM data file under /system32/config. I even tried to delete it but that did not helped
Hummm now what to do ? I googled again and used the programe “OPHCRACK”
Recovery process 2: (OPHCRACK)
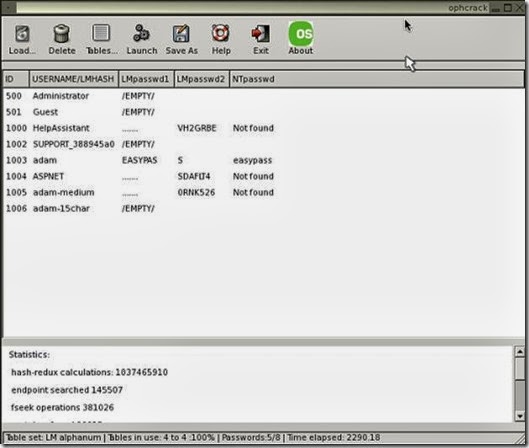
This method is bit lengthy but this also did not helped me . You can find this program over http://ophcrack.sourceforge.net/ . It has 500MB ISO file which you need to burn on CD (in my case I used USB ) and then boot the machine using this. Some one has already posted the screen shot attaching it here
Drawback for this programe is
1. Need to download big 500MB ISO
2. You need to wait till it crack it
3. You can Only see the password but can make any changes (May be I don’t know anything special).
In my case it just showed as empty. I tried the blank password and that did not help.
Recovery process 3: (The LOGON.SCR trick)
I tried this http://www.petri.co.il/forgot_administrator_password_alternate_logon_trick.htm but did not read this
Note: The information found on this page is valid ONLY for Windows NT 4.0, and for some earlier versions of Windows 2000 (prior to more advanced service packs). DO NOT ATTEMPT TO TRY THIS ON WINDOWS XP PRO MACHINES, you will only waste your time.
To successfully reset the local administrator's password on Windows NT and some versions of Windows 2000 follow these steps:
1. Install an alternate copy of Windows NT or Windows 2000.
You must install this instance of NT/2000 on a different folder than WINNT, otherwise you'll end up with the same bad situation. Use ALTWINNT for example.
It is best that you install the alternate instance of the OS into a different partition than the one you have your original installation. You'll delete this folder anyway, and it's best that you just format that partition after you're done. Formatting the partition will be much easier than deleting individual files and folders.
Also, if you lost your password on NT - install a new instance of NT, not Windows 2000, as doing so will ruin your old NT installation (because of the difference between the NTFS versions). Same goes for W2K, XP and Windows Server 2003. Always install the same OS.
Note: On Windows NT 4.0 machines that were installed out-of-the-box you do not have to install a fresh copy if you still have access as a regular user to the system. E.g. if you can log-on as a regular, non-administrator user, you can still manipulate the file's permissions. This is simply because NT's default permissions are set for Everyone - Full Control. This is not true on W2K/XP/2003 machines.
Another note: Reader Mike wrote:
In the article you mention installing the OS on top of the existing OS to do the logon screensaver manipulation.
I wanted to mention that this can also be accomplished by removing the hard drive, placing it as a slave on another computer (XP and W2K play nicely) and then accessing the file system. Of course you need a second computer, but for some folks it may be an easier solution.
Thanks,
Mike
That's correct, and it will work for you unless you converted the disk to a dynamic disk, on the original OS. In that case you will no longer be able to boot the old OS, even if you do manage to access the files from the other computer.
2. Boot the alternate install.
3. Use Control Panel/System/Startup (for NT) or Control Panel/System/Advanced/Startup and Recovery for W2K to change the default boot instance back to your original install.
Lamer note: If you don't do that you'll end up booting into the alternate installation next time you turn on your computer. You don't want that, do you?
4. Open Explorer. Browse to your original Windows NT/2000 folder, navigate to the %systemroot%\System32 sub-folder.
Lamer note: %systemroot% is a system variable used to point to the folder where NT/2000 is installed, usually \WINNT in NT/2000, or \WINDOWS in XP/2003.
5. Save a copy of LOGON.SCR, the default logon screen saver, anywhere you like. Just remember where you've placed it. You can also just rename the file to something you'll remember later, I user LOGON.SC1.
Lamer note: To rename a file use the REN command in the Command Prompt window, or just select the file in Windows Explorer and press F2.
6. Delete the original LOGON.SCR from the %systemroot%\System32 sub-folder. It is not necessary to delete the file if you renamed it, you can leave it there.
Note: You might not be able to delete the LOGON.SCR file because of permission settings. Regular users can only read and execute the file, not delete it. If that is the case (and it is in W2K, XP and Windows Server 2003) then you need to take ownership of the file and give the EVERYONE group FULL CONTROL permissions.
Lamer note: In order to take ownership of a file right-click it, select Properties, select the Security tab, click Advanced, and then click on the Owner tab. Select one of the users found in the list, click ok all the way out.
In order to change the LOGON.SCR permissions follow the previous instructions, in the Security tab click Add and browse to the Everyone group. Add it and make sure you give it Full Control. Click Ok all the way out.
7. Make a copy CMD.EXE in the %systemroot%\System32 sub-folder. CMD.EXE is located in %systemroot%\system32.
Lamer note: In order to copy a file via GUI, select the file, right-click and chose Copy, then go to the destination folder, right click the folder name and select Paste. You can also use the keyboard by typing CTRL-C to Copy, CTRL-V to Paste.
8. Rename the copy of CMD.EXE to LOGON.SCR.
Lamer note: See step #5.
9. Shutdown and restart your computer. Boot into the original install.
10. Wait for the logon screen saver to initiate - around 15 minutes. Oh, and no, do NOT move your mouse while you wait, duh...
After the screensaver is initiated, instead of running the normal LOGON.SRC actual screensaver, it will run the renamed CMD.EXE file (which is now called LOGON.SCR), and will actually open a CMD prompt in the context of the local system account.
In step #7 you could have used EXPLORER.EXE instead of CMD.EXE, and in that case a My Computer window will pop up.
Note: As noted earlier on this page, there is a way to make the wait time shorter, but you'll need to dig into the Registry for that.
11. Open the CMD.EXE prompt (it should already be opened if you've used CMD.EXE in step #7) and type:
net user administrator 123456
This will reset the local administrator (or domain admin if you are doing this trick on a DC) password to 123456.
Lamer note: You can, of course, use ANY password you want...
12. Delete the LOGON.SCR from %systemroot%\System32.
13. Rename the saved default screen saver from step 5 back to LOGON.SCR.
14. If you wish to remove the alternate install:
● Delete its' folder.
● ATTRIB -R -S -H c:\BOOT.INI
● Edit c:\BOOT.INI and remove the alternate install's entries.
If you've used a different partition to install the alternate install then now you can simply delete or format that partition if you don't need it anymore, plus edit c:\BOOT.INI and remove the alternate installation entries.
This trick has been tested a zillion times. Don't bother to tell me it doesn't work, it does (for Windows NT and some versions of Windows 2000), and that's a fact.
Recovery process 4:
Finally I tried this and WOW it worked like a GEM
ERD is an excellent multi purpose product, but you should know it is not a necessary one if you have a healthy system and your sole problem is the inability to logon to Windows due to a forgotten password. Not necessary because you can easily change or wipe out your Administrator password for free during a Windows XP Repair. Here’s how with a step-by-step description of the initial Repair process included for newbie’s.
1. Place your Windows XP CD in your cd-rom and start your computer (it’s assumed here that your XP CD is bootable – as it should be - and that you have your bios set to boot from CD)
2. Keep your eye on the screen messages for booting to your cd Typically, it will be “Press any key to boot from cd”
3. Once you get in, the first screen will indicate that Setup is inspecting your system and loading files.
4. When you get to the Welcome to Setup screen, press ENTER to Setup Windows now
5. The Licensing Agreement comes next - Press F8 to accept it.
6. The next screen is the Setup screen which gives you the option to do a Repair.
It should read something like “If one of the following Windows XP installations is damaged, Setup can try to repair it”
Use the up and down arrow keys to select your XP installation (if you only have one, it should already be selected) and press R to begin the Repair process.
7. Let the Repair run. Setup will now check your disks and then start copying files which can take several minutes.
8. Shortly after the Copying Files stage, you will be required to reboot. (this will happen automatically – you will see a progress bar stating “Your computer will reboot in 15 seconds”
9. During the reboot, do not make the mistake of “pressing any key” to boot from the CD again! Setup will resume automatically with the standard billboard screens and you will notice Installing Windows is highlighted.
10. Keep your eye on the lower left hand side of the screen and when you see the Installing Devices progress bar, press SHIFT + F10. This is the security hole! A command console will now open up giving you the potential for wide access to your system.
11. At the prompt, type NUSRMGR.CPL and press Enter. Voila! You have just gained graphical access to your User Accounts in the Control Panel.
12. Now simply pick the account you need to change and remove or change your password as you prefer. If you want to log on without having to enter your new password, you can type control userpasswords2 at the prompt and choose to log on without being asked for password. After you’ve made your changes close the windows, exit the command box and continue on with the Repair (have your Product key handy).
13. Once the Repair is done, you will be able to log on with your new password (or without a password if you chose not to use one or if you chose not to be asked for a password). Your programs and personalized settings should remain intact.
Let met tell you I have spend 20 whopping hours to figure which method really work so you have to believe me. This method work like a gem and you will not loose anything. I was doing all these not to recover my password (as I already backed up my data) but to figure out there might be a way to recover the password










No comments:
Post a Comment