Where we use this : Let’s say I am publishing my resource via NetScaler AGEE and would like to ensure that user should be bind to the PC while accessing resources externally from non corporate device. For my use case , it was external users who uses dealer management system to update inventories. We choose this method over all the available options like
a) Symantec MPKI b) Two factor Authentication c) Smart Card
One of the reason why we choose below method was for simple reason, it doesn’t evolve extra cost.
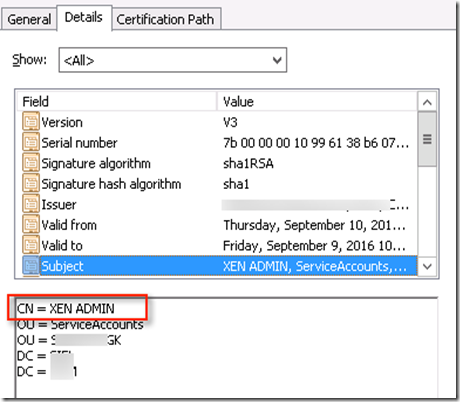
To start with we setup enterprise CA on MS windows 2012 R2 server. You will get enough document on how to install CA but I will cover what we needed for this specific use case. We wanted to ensure that user certificate generated is in PFX format. Also we had challenge with given name in AD. When certificate generated based on given name CN it would look like this
When CN is checked for certificate via NS profile
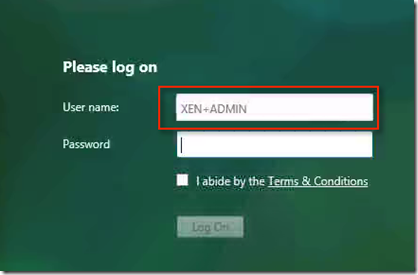
It use to put + in place of space like this
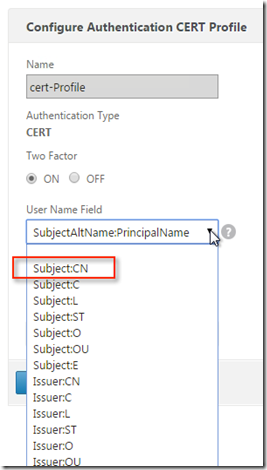
Now it is important that certificate must be generated with SPN name
By default CA doesn’t generate certificate using UPN and attribute must be inputs. So let’s discuss how we setup CA to generate user’s certificate with attribute. To generate CA certificate for users, information must be filled manually. CA doesn’t allow certificate to be generated manually hence template properties needs to be set properly. To create certificate template select certificate templates and choose manage under certificate manager.
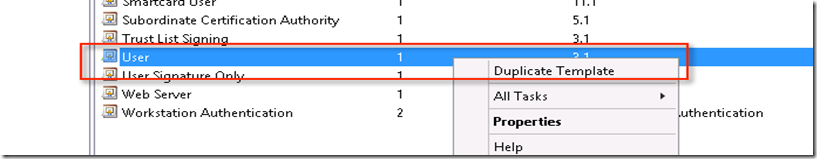
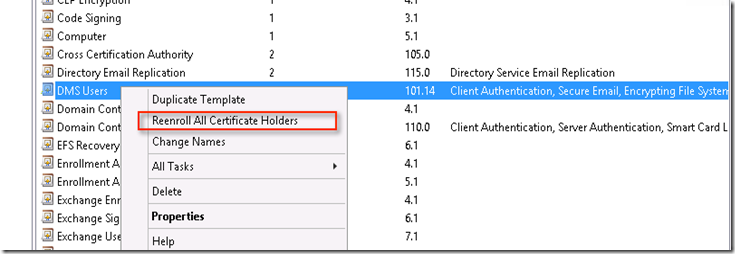
This will open certificate container which will have list of certificate which can be duplicated. Here we have to choose “Users” certificate then duplicate it. Remember while doing this, ensure that you have logged into appropriate ID since this changes are at Domain level. I have chosen Domain Admin to make changes
Once certificate is duplicated, it needs to be enrolled into all the certificate holders. Here I have chosen enrolled certificate hence option is “Reenroll All Certificate Holders”
Set the template properties for subject name to manual so it will allow to generate certificate for multiple users. Here we can define certificate validity period
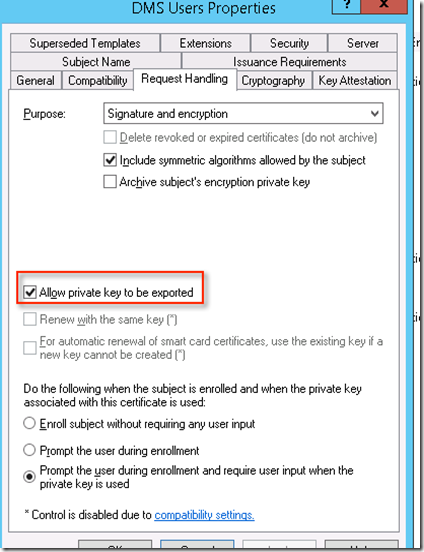
Set the certificate for “Request Handling ” to “Allow private key to be exported”
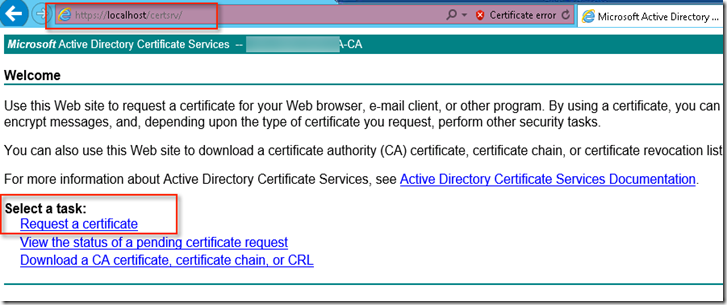
Now when we browse certificate manager URL and then choose “Request a Certificate”
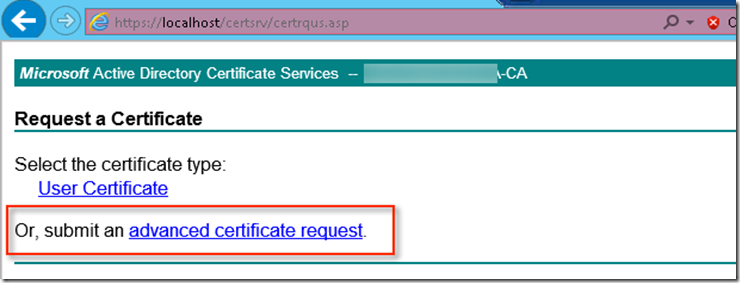
Then choose “Advance Certificate request”
Then choose “Create and Submit a request to this CA”
Choose correct template under drop down
Under Attributes supply SAN as SAN:UPN=Username@domain.com which matches the logon name of the users under users manager
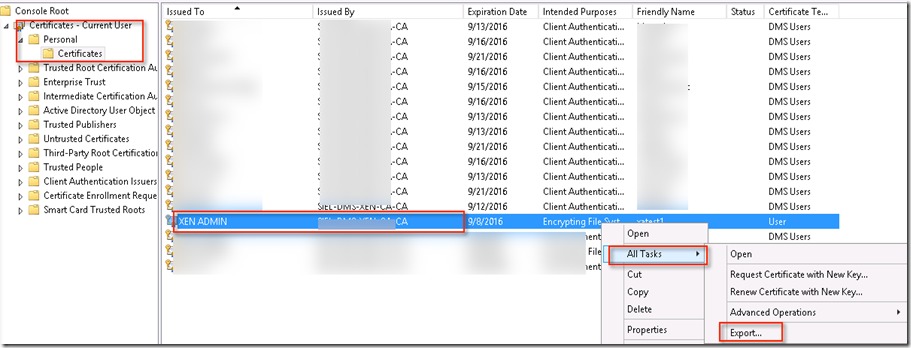
Once certificate is created, it will be present under certificate manager then it will provide option to export into PFX format
Choose private key and then choose password to export the certificate. Same password will be used to import.
Once certificate is installed on client machine this will appear under Personal which can be viewed via IE – Internet option – Content – Certificate . If this doesn’t appear here then it will not work. In the next section we will discuss what setting is required on NetScaler.
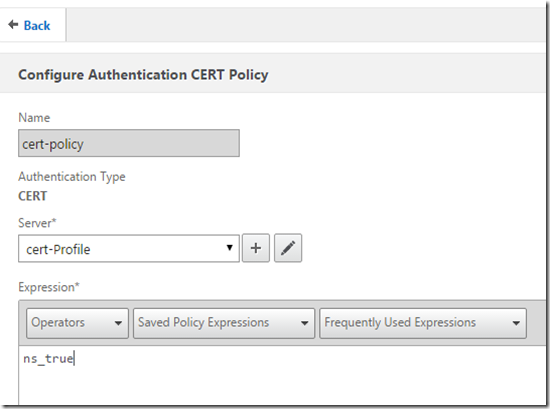
In this case, I had been using NetScaler build 11.0 55.23Build . So will start with creation on certificate policy . For that we will create certificate profile with two factor ON and user name field as UPN and followed with policy to be set to ns_true
Once Policy is ready it need to bind to the AGEE vServer as primary authentication as Cert policy
Now SSL parameter needs to be set to client certificate to “Mandatory”
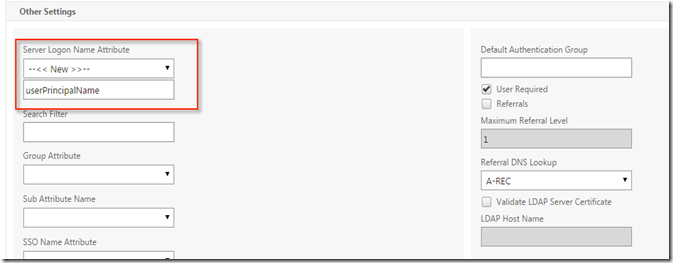
Since we have using client UPN for the login, LDAP policy must be set to use “userPrincipalName”
Now when client type the AGEE URL for access it will prompt to select client and if machine has multiple client certificate it will provide option to choose. Below example shows machine had multiple certificate and it prompt users to choose
Once users choose the certificate users name will populated and all the users will have choice to type password
Post login and application is launched it will prompt to choose the certificate. Below example users try to launched notepad and it prompt users to choose certificate. This is known behavior and one would like to fix this can follow CTX200193. There are otherway which I am yet to test.
NOTE of caution : At the time of writing this blog, it was found that client certificate doesn’t work with native receiver . So if you have the use case where customer would like to use both native receiver and browser then avoid to choose this option.






















2 comments:
There is much simple method is available with client certificate
which we implemented
If you know better way please do share it. I will be happy to take a look and try it
Thanks,
Vikash
Post a Comment